1. Introduction
The vehicle ad hoc network (VANET) is composed of the mobile entity called vehicle and fixed entity known as Road Side Units (RSUs). The entities exchange of messages through the three modes of communication namely vehicle-to-vehicle (V2V), vehicle-toinfrastructure (V2I) and hybrid communication [1]. The VANET intelligent applications depend on the exchange of messages between the entities source and destinations [2]. Consequently, these messages confront challenges evaluation trust of the data and entity to obtain insufficient attention. To protect and preserve the system from of these various attacks and the entities which commit it. The most common attacks in VANET are: Sybil attack, Newcomer attack, Blackhole attack, etc [3].
The security of the communication concentrates about trust in data exchange during communication, which is based on the concept of trust model to improve the security of communication. These trust models face some challenges must be considered against malicious vehicle that leads to the most critical and challenging security issues. The destination of the vehicle ensures that messages received come from the same source it claims. The biggest problem is that the vehicle must check the message integrity as fast as possible for avoiding the influence of real rate of data in the network. The movement of highspeed vehicles and the high density of traffic allow congestion on the road. Therefore, destination vehicles receive a lot of data but the problem of waiting for confirmation to detect falsifies the position and the actual times to respond [4,5].
The trust model permit mitigates these risks, which manage accurately trust between vehicles, used for making a decision as to follow the message or no. Working with a specific trust model it achieves security resiliency and robustness in the presence of malicious node sending false information to misguide other nodes. Trust management scheme will not allow malicious nodes to increase the trust value of untrustworthy message. The trust value obtained in the non-malicious environment will always be greater than the trust value obtained in the malicious environment [6,7].
2. Related Work
In this section, we will present the different trust models, which helps to ensure trust between entities and data, i.e. the reliability of messages and malicious entity blocking. These trust models can be classified into three categories of vehicle networks and listed as below: (A) entity-centric, (B) data-centric, and (C) combined.
2.1 Entity-oriented trust model
In this approach, we describe the models that are based on the reliability of the entity (vehicle), which is based on obtaining information about the sender and neighbor receivers. However, the change of vehicle position allows frequent interruptions, which makes difficult to have sufficient information about the neighbors.
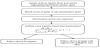
The authors of [8] propose a VANET Dynamic Demilitarized Zone (VDDZ) trust model that uses a public key infrastructure and distributed cluster algorithm. As shown in Figure 5. The objectives of the trust model VDDZ is to exclude the entry of malicious or obscure vehicles in cluster, it prohibits using directly the communication of a cluster head (CH) with other member vehicles. This technique represents a set of registration authority (RA) vehicles located 1-hop away from the certification authority. This cluster algorithm uses two parameters:
- The trust metric (Tm): allows calculating confidence it for each vehicle.
- The mobility metrics: preserves security and stability of cluster head.
The Head cluster determines the trust level of vehicles in the cluster by a trust metric. The (Tm) is a continuous value between 0 and 1. Of course, new vehicles start with Tm = 0.1 and all vehicles with Tm <1 must behave well to increase their trust metric. Trusted vehicles are those with Tm = 1 [9], and this algorithm uses two types of messages:
- The HELLO message, consisting of speed, identity, position, current status, Tm table and current neighbors.
- BEACON ELECTION, consisting of an IP address, number of hops, relative mobility (RM) and number of trusted neighbors (NTN). Figure 1 describes a VDDZ.
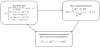
The Trust and Reputation Infrastructure-based model (TRIP) is presented in [10]. This model can detect malicious nodes that broadcast erroneous messages over the network. As shown in Figure 2, the malicious nodes are isolated by trust and reputation. Fuzzy sets [11] are sets where a member can have partial membership. This model utilizes fuzzy logic for to determine the trust values. Scores are evaluated based on three pieces of information:
- Latest interactive experiences between the nodes,
- The vehicles to neighbors,
- Recommendations from other central authorities.
The confidence value of the vehicle is evaluated by three levels:
- "TRUSTED" vehicles are accepted and their traffic warnings are broadcasted for other vehicles.
- "+/- TRUSTED" vehicles are accepted and their messages are issued as trusted vehicles but it is not transferable.
- "NOT TRUSTED" vehicles are rejected and their messages warn the presence of a malicious vehicle
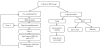
Zhouw et al. [12], proposed a Dynamic Trust Token (DTT) mechanism that focuses on finding uncooperative network nodes and ensuring the integrity of the package upon delivery. This mechanism uses symmetric and asymmetric cryptographic algorithms and Neighborhood WatchDog algorithm to protect the integrity of the packets. In this algorithm, packet monitoring increases during communication for security packet. The initiator must be trusted and the event package is right when it is generated. This packet transmits for routing to neighbors during a transmission session. Each transmission session (TS) is framed in a time interval, which increases the latency for receiving in the network. The disadvantage of this mechanism does not excite changes on malicious behavior, do not prevent malicious nodes. Figure 3 describes a DTT.
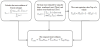
In [13], the authors propose a solution called Multi-faceted Approach to Modeling Agent Trust permit the reliability of the agent to behave honest behavior. Thus, the trust of an agent is based on two parts priority-based trust and the majority-based trust. In addition, the priority based is used to select in preference between other agents/ vehicles. Following this, it divided in two parts on trust based on experience-based, role-based. The role-based is basic some vehicles have high trust such as the police for to relies on the identification of agents (vehicles). Trust based on experience is used with the past interaction. The majority opinion is also used to group the selected comments. Moreover, each node calculates the trust values through previous experiences.
An agent may passively wait for other agents to report on an event. In fact, every agent contains in database, with the aim of containing list of past interaction them. But usually, the agent sends a request to a list of neighboring trusted agents to inquire. But it may be necessary to verify this information by interviewing other trusted agents. The agent must aggregate the shipper's reports and the officer will decide whether to believe a particular report and take the corresponding action. Figure 4 shows Multi-faceted.
Jorgeh et al. propose in [14] the trust establishment that utilizes watchdog algorithm with intrusion detection techniques. The watchdog technique can be described to detect routing perturbation attacks in ad hoc networks. It aims to guarantee protocol independent, and a useful instrument for intrusion detections in ad hoc networks.
The objective of the watchdog is to monitor packets in order to take into consideration routing rule. The watchdog of a particular node transmits data to the node’s neighbors in order to observe the routing protocols. The watchdog computes all the received packets for defining a node that exhibits a malicious behavior. A neighbor trust determines the received packets for forwarding and those effectively forwarded by the neighbor node. Drawback of this technique is to differentiate the loss of a packet that due to an attack or a collision. Figure 5 describes a watchdog.
2.2 Data-oriented trust model
Confidence modeling is about data reliability. Data-centric trust can be termed event-based trust. This model estimates the level of trust of each sender and receiver. As a result, the high traffic density increases the amount of data, which leads to a risk of long latency for data transfer and network disconnections.
In the study [15], the authors propose a model of trust based on clustering with Ant Colony Routing (TACR), Clustering is created by the algorithm based on position, direction and velocity. There are two cases for the Cluster Head (CH) selection:
- If the RSU is present it will be chosen as CH,
- In case if RSU is absent of, the algorithm searches and select the slowest vehicle of the cluster, as this guarantees coverage for a maximum period.
The goal of the cluster head (CH) is to guarantee the real-time dissemination of data with the value of trust between the sender and the recipient. The new vehicle starts with the normal value trust.
The trust value is calculated directly and indirectly; the direct trust is obtained for each vehicle by transactions with neighboring vehicles. It depends on several parameters: Traffic RuIe Obey (TRO), Data Packets Forwarded (DPF), Data Packet / Message Precession (DPP), Control Packet Forwarded (CPF), Control Packet / Message Precession (CPP). The indirect trust used at the Cluster-Head level to calculate the trust value of strange vehicles generates messages. Indirect trust value does not allow malicious vehicles to send messages across the network. Figure 6 describes a TACR.
The authors present in [16] a model of trust centered on the entity that allows discovering the black-hole attacks and the reliability of the data transmission. As shown in Figure 7, trust is based on three parameters: Direct trust, Recommendations and Comprehensive trust.
The value of direct trust is calculated according to the data transfer rate and the weight of the data, which must fulfill these three conditions: Traffic Safety, Traffic Efficiency and Infotainment Data, which have different impacts on the data traffic. The value of the recommendation trust is determined by the direct trust value of the source node to its neighbors and by the global trust value of other neighbors with the destination node. Comprehensive trust is a combination of two parameters of direct trust and trust recommendation that has a different impact on network nodes already in use. The direct trust will not be important the recommendation trust. The node strange is request to use the recommendation. This model builds to apply security on the GPSR routing protocol and increase the rate the transmission of success data.
The authors of [17] propose an information-driven Real-time Message Content Validation (RMCV) trust model that allows each vehicle to evaluate the reliability of a large number of messages received in VANETs. They use several factors that have a huge impact: evaluating the reliability of messages, such as content similarity, content conflicts, and similarity of the message routing path.
As shown in Figure 8, the RMCV scheme includes an information-oriented trust model; it also includes a message classification component to identify messages describing the same event. The potentially high number of received messages can be grouped together using clustering algorithms. First-level clustering generates a collection of messages describing the same event based on the content. The purpose of the second level is to identify conflicting information about the same event.
The information-oriented trust model is to determine which collection should be approved. The confidence score of each message will be calculated at the level of each vehicle.
There are group of messages that are associated with the same event, similar messages are generally considered as mutually supportive group. This is an important factor in judging the reliability of a message. Modeling the effects of these two important parameters can be used to determine:
- The maximum distance of the content between two messages in the same cluster.
- The number of messages in the cluster.
The authors of [18] propose trust model based on identity anonymous vehicular ad hoc networks, this model also allows detecting false location and time information.
The intrusion-aware trust model is based on three phases:
- The first phase estimates the confidence value for every received message.
- The second phase estimates the trust value for every single message.
- The last phase makes the decisions on the message, mainly based on their highest trust value.
As shown in Figure 9, the trust value is measured by using the following four parameters: The location closeness, time closeness, location verification and time stamp verification.
The parameters can be calculated without knowing the source identities. The trust value is based on the total number of sender nodes and confidence value. The decision logic is based on two steps:
- In the first step, the system takes the messages that have the highest trust value.
- The second step, the system makes the decision to approve that message if the trust value of the selected message is greater than the minimum acceptable threshold.
In [19], the authors proposed a trust model namely Road side unit Aided Trust Establishment scheme (RATE). The RSUs has been considered to execute the trust establishment, which separatethe dataconsuming vehicles from those submitting information. This model uses the Ant Colony Optimization ACO algorithm, which evaluate trustworthiness of data. The ACO main objective combines the direct observed data with feedback information.In addition; the vehicles create the observations and confidence according to the detection of an event. The estimation of the Observation Factor is based on the most recent reporting frequency of the evidence. The observation factor is calculated according to the confidence of the observer on this piece of evidence and the weight corresponding to reporter’s identity. The feedback factor denotes the directory's practically verified usefulness. The management of feedback depends on three stages: initialization, aging and promotion.
The RSU receives observation reports. RATE has put them in the recently received observation list (Lro). The RSU allow testing the recent observation reports in (Lro). The observation factor estimation is based on all the confidence and weight. The confidence is established by the distance from the vehicle to the event k (Dk), maximum detection range of the vehicle (Dmax), the number of sensors that can detects the event (Nks), and total number of sensors equipped in the vehicle (Nmax). Besides, the weight of vehicle is determined by the type of vehicle. Figure 10 describes a RATE.
Cong et al. [20] proposed trust model based on the estimated trust of the originator or forwarder, which aims to determine the accuracy of V2V incident reports. In this model, the trust score is estimated by using the behavior history of incident report accuracy for the vehicle, based on this, a trust model is used by Vehicle Behaviour Information collection Infrastructure (VBII) to provide a central authority incident reports received from other vehicles. To ensure the viability of the process we consider three assumptions:
- The latency: describes the period of delay of traffic incidents in real-time.
- The vehicles observe the behavior of other vehicles to transfer the information to the central authority.
- The identifier system for vehicles that contains other vehicles information.
As shown in Figure 11, the vehicle takes trusted decisions from the information received based on the confidence score. The trust score of the report originator and forwarders allows taking two decisions:
- The vehicle makes the decision on whether accepting or not the data message from other vehicles.
- In the case where the vehicle decides to accept the received information, an endorsement opinion must be attached.
2.3 Combined-oriented trust model
This model depends on the estimation of the reliability of the data based on the trust of the entity. It checks the confidence of the received data, using its previous experience of reliability received from other vehicles in the network.
In [21], the authors present the hybrid trust modelthe basic distributed public key infrastructure and algorithm Fuzzy. Thetrust depend two aspects to follow:The cooperation between vehicles disseminates the reliability data. Consequently, the cooperation depends on the estimate to receive a warning message by the reputation of the same event. The surveillance the behavior of vehicles used Fuzzy algorithm, which can filter malicious vehicles.The trust estimates that level by the trust metric (Tm), which consists of interval value in [0, 1].The vehicle assess trustworthiness arrive 1. The trust level is refreshed with every change in cluster. The Certification Authority (CA) is responsible for creation the certificate among the member of the cluster. Figure 12 describes a Fuzzy.
The authors in [22], propose a mechanism for estimating the trust value based on the behavior of each vehicle, which concerns data integrity protection through the hashing technique and use a trusted path. The value of the trust evaluates the periodic message broadcast with its acknowledgment.This mechanism allows the evaluation of the trust value by each vehicle, which will calculate the confidence value and transmits it to the AS via RSU. Then the AS will save the trust values and broadcast them immediately into the network via the RSU.This mechanism allows the evaluation of the trust value by each vehicle, which calculates the confidence value to transmit the value to AS via RSU. AS depends on saving the confidence values immediately broadcast in the network through RSU. This mechanism identifies the valid RSU node to apply the hash technique on the data, every vehicle containing a value of confidence using this value to discover trusted paths to transmit information via trusted nodes. The disadvantage of this mechanism is that it does not check the behavior of periodic messages. Figure 13 describes a Hashing.
Hamssa et al. [23], proposed a hybrid trust model based on a public key infrastructure and allocation to determine the most reliable vehicle defined as the group leader (GL). The model manages the communication between the members and references all the exchange information in the cluster. This model estimates the value of trust in direct / indirect way to build an evaluation of a total trust.The vehicle that has which the highest of the trust value used as though Group Leader. The RSU given for every new vehicle authenticate. Consequently, the new vehicle contains value of confidence called trust initial. The vehicle broadcasts a message containing a direct trust list for its neighbor, whom will use it to calculate indirect trust. Then, the trust value of the vehicle is sent to the GL, which in turn will send its trust value to the RSU. Figure 14 describes a GL.
In [24], the authors proposed a Beacon-Based Trust Management (BTM) system, which prohibits the internal attackers from sending false messages and privacy enhancement. The system estimate a hybrid trust by cross-checking the plausibility of event messages and beacon messages, which computes entity trust by using beacon messages and evaluate data trust by the determination of event messages and beacon messages.
In this model, secure beacon based trust protocol is used to estimate direct and indirect trust. In order to calculate the direct trust observed by a vehicle itself or neighboring vehicles, that evaluates the first-hand information by position and movement verification. Indirect trust is obtained via the recommendations from other vehicle. Entity trust uses cosine similarity for to estimate values by position, velocity, and direction. The reputation value is calculated based on the indirect event trust value where the previous reputation value is considered. Data trust is based on direct event based trust and on indirect event based trust. Figure 15 describes a BTM.
3. Evalution of Trust Models
In this section, we will describe the properties to take into account for the trust models mentioned above, which imposes big challenges and constraints to take into consideration.
3.1 Dynamic
The vehicle ad hoc networks have the properties fast moving and the variable densities on the road. The rapid movement of vehicles disrupts communications, causing frequent interruptions. This makes it difficult or impossible to obtain this information such as identification and position of the vehicle because it will not stay in a few seconds. The density varies depending on the number of vehicle sometimes very high or very low depending on road situations. The high density increases by the number of vehicles on the highway preserves the available connectivity. On the other hand, the low density is measured by the numbers of the vehicles diminishing on the highway causing breaks disconnections. Low density leads to a long waiting period risk for routing. Therefore, we use these definitions to compare trust models.
3.2 Decentralization
The vehicle can at any time join or leave the network at random, which is a major drawback for the centralization of trust management. The establishment of trust must be achieved without the existence of a centralized infrastructure. It is a requirement for a decentralization environment.
3.3 Security
Security is several required such as authentication and encryption / decryption method. The authentication is established through the reliability of messages when sending the message. In addition, the authentication is an important step in building trust and revealing the true identity of peers. The cryptography technique is a very important parameter to guarantee secure communication. The results estimate security incapacity in trust models.
3.4 Privacy
The information of location and identification of the vehicle considered as the most critical information. This information privacy allows decided the trust of a vehicle via its identity, once its identity authenticated, position and its own honest behavior is verified, we can trust the information received by this vehicle.
3.5 Real-time processing
In VANETS, delay is strictly intolerant. The power of trust management is in providing security based on real time communications. If a required message could not be received in time, that could pose certain problems facing the accurate establishment of the correct trust value for the sender, which requires a real time and high performance for processing units in the infrastructure [25-27].
4. Discussion
In the previous section, we describe in detail the existing trust models in VANET environment in Section II. The trust model defines three categories as such: (A) entity-centric, (B) data-centric and (C) combined. The applications in VANETs are based on the shared information between the entities. The different applications are exposed to some security attacks, even if the target is a specific service, for sure other related services will be affected as well. The VANETs applications are classified according to their: safety, security, and infotainment [28]. This classification of applications presents different impacts of each type of attack.
The trust is adopted for secure the network and ensure the integrity data against the different threats either dishonest entities, malicious messages, or both. In other words, the trust defenses against the inside attackers in those situations where cryptography completely fails. Based on this model, we observed the trust model concentration on the properties and the trust metrics. Consequently, the trust metrics define precisely for requirement to need the properties of the trust model. Therefore, this model is based on evaluating the properties of the trust model. According, the trust models design to evaluate the entity and reliable data in the VANET network. In addition, we will present the properties of criteria need for the trust management, to make a comparison between the models of trust with the properties in Table 1.
The different requirements must be enough of the properties elements in the trust models to avoid the large number of more targeted attacks. We above present the results of our evaluation concerningthis list of properties, namely dynamic, decentralization, security, privacy, real-time.
This result shows that trust models have the insufficient of effectiveness for the list of properties. Form this table, we note that none of the trust models apply all properties, in fact, the trust model has not focus the privacy ignore this properties by the researchers.
5. Conclusion
The trust model allows evaluating trustworthy entity or messages, which reduces the risk misbehavior vehicles during the communication. The evaluation of trust is so important to assure secured communications in VANET. The trust management has been proposed in the last years as an accurate alternative to deal with some security threats in highly distributed and dynamic scenarios. In this paper, we present survey the trust model for the networks VANET domain. Thus, we will describe in detail of the several trust model. Accordingly, the trust models distinguish three categories as follows: (A) entity-centric, (B) data-centric and (C) combined. We chose thislist of the properties to evaluate the effectiveness of the trust model. Then we will describe all the property in the list as follows: dynamic, decentralization, security, privacy, real-time. In this study we discussedthe comparison trust model with the list of the properties. Based on this result, we allow us interested to the trust management in the network VANET, more particularly in a context the trust of data.
In future work, we will propose a new approach to the trust model that can detect and mitigate entities and malicious behaviors in VANET networks.
Competing Interests
The authors declare that they have no competing interests.
Author Contributions
Acknowledgments
This research was supported by the University of Paris-Seine, France, and the Algerian Ministry of Higher Education Fellowship awarded to Nourelimane Bousmaha.
The information provided in this paper is the sole responsibility of the authors.